Every now and then, one of my customers comes back with something they've been working on. In this case, it's Ben North showing some work he did modeling the Colossus code-breaking machine built at Bletchley Park.

First, Ben had to understand how Colossus actually broke codes. He did this by creating a Jupyter notebook that replicated the process of encrypting some plain-text (in his case, Dicken's Pickwick Papers) with a Lorenz cipher and then analyzing it as Colossus did. Doing this, he was able to debug his understanding of each step in the algorithm. He shows how a small feature of the Lorenz cipher (that the encryption wheels do not always advance after each letter) leads to an observable distortion of the letter frequency in the encrypted text which can be used to guess likely settings for the wheels.
Once the operational details were understood, Ben went about implementing (most of) Colossus in the Spartan-6 LX25 FPGA of a XuLA2 board. He created VHDL code describing each portion of Colossus. These pieces communicated with a dataflow protocol (i.e, a unit would start processing if it had data available in its input buffer and space available to hold the result in its output buffer). Because of this loose coupling, it was relatively easy for Ben to add multiple analysis pipelines to his design.
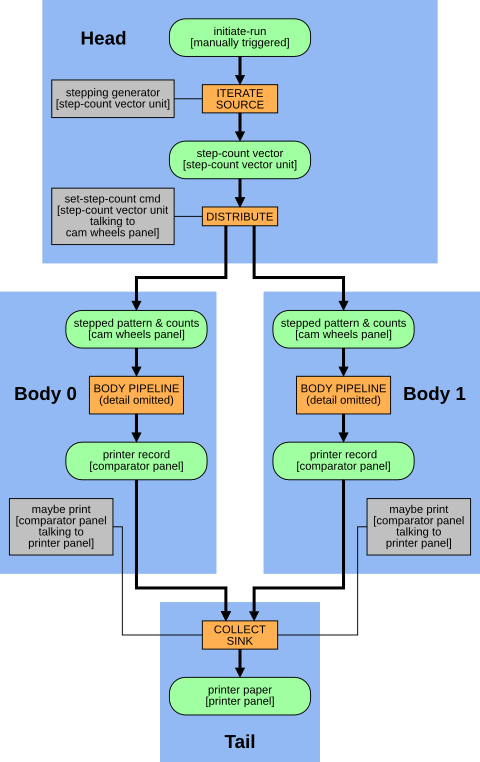
To test his design, Ben wrote unit tests in Python that drove a simulation of his VHDL code. When it came time to test the real thing running in the FPGA, he just changed his unit tests so they interfaced with the Raspberry Pi GPIO pins connected to the XuLA2 board.
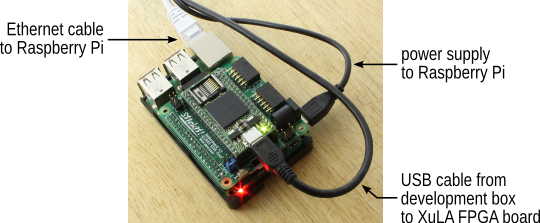
The results from the actual hardware test matched with the simulation on the first attempt. According to Ben, he found this a "satisfying outcome". I guess he picked up a penchant for English understatement while working on this project.
For those looking for a project, it would be great to recode Ben's VHDL into MyHDL. Then it could be included in the same Jupyter notebook with the Lorenz encryption/decryption theory, and the tests could be run using only Python with no need for the VHDL simulator. You could probably also get dynamic animations of the Colossus pipelines that Ben had to hard-code in his documentation.
Some colossal work here, Ben! Thanks for sharing it.
(Figures: Ben North, used under CC BY-SA 4.0)
Share on Twitter Share on Facebook Share on Reddit
Comments
New Comment